Hard drives fail. All of them…eventually.
I love my iMac, It is a finely crafted piece of aluminum that greets me everyday with a beautiful bright glow and serves me well, even when I force it to run windows on occasion. For many it is the central hub of their home and/or professional computing universe. If you are not backing up your system with Time Machine you are really playing with fire. For the cost of a cheap terabyte external drive (usually less than $100) you can recover from the inevitable hard drive crash, quickly and with less expense.
For those that like to throw caution to the wind let me paint an all too familiar scenario. “Good afternoon Computer Doctor, how can I help you? Oh hi, I have a problem with my mac, for the last couple months it has been really slowing down, updates don’t work and every once in awhile it freezes up, this morning it won’t start at all. All I see is a grey screen with a folder with a question mark. In response I ask if they have a back up. No, I have been meaning to get one of those, I really should one of these days.
From there it can go from bad to worse quickly. Replacing the hard drive on an iMac requires removing that glorious screen and digging deep into the heart of the system, this in itself is not for the faint of heart… Once replaced if there was a back up, the system could be restored to the last place in time where it was functioning correctly and all your pictures, movies, iTunes documents will be right back where you left them.
Without a backup, What can happen if your lucky, is a piecemeal recovery which can be very time consuming, followed by a new installation of OSX and then all your apps. That is if the drive is intact enough to extract data. If it isn’t there are techniques to coax the data out and some very expensive recovery solutions that require a clean room and a pocket full of cash.
If you are in the greater Bangor, Hampden region and are experiencing crashes, freeze ups, shut downs, grey screens and the “spinning beach ball of death” Call or email me @ Computer Doctor of Hampden, sooner than later and we can get your beloved iMac back in great shape. If it is running fine, please stop on the way home and pick up an external drive. You will thank me later!





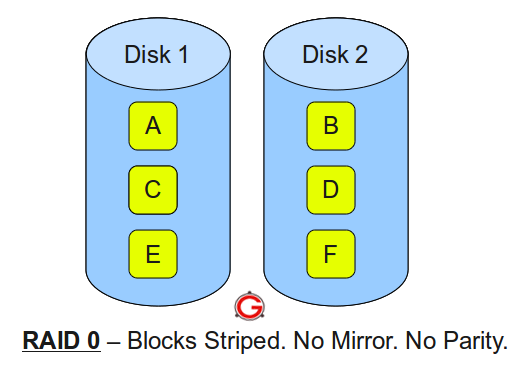
 Following are the key points to remember for RAID level 1.
Following are the key points to remember for RAID level 1.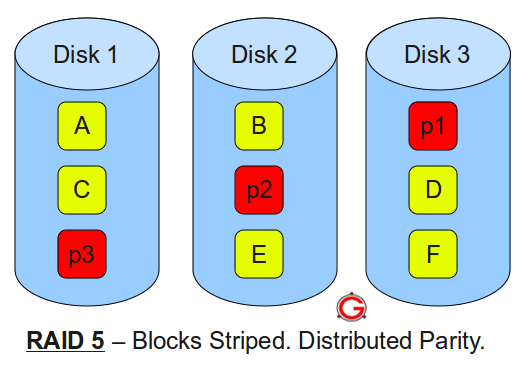


 So your hard drive just died, and you didn’t back it up. I’m so, so sorry. You can expect to go through the following five stages once you discover that all of your photos, files and music are gone forever.
So your hard drive just died, and you didn’t back it up. I’m so, so sorry. You can expect to go through the following five stages once you discover that all of your photos, files and music are gone forever.